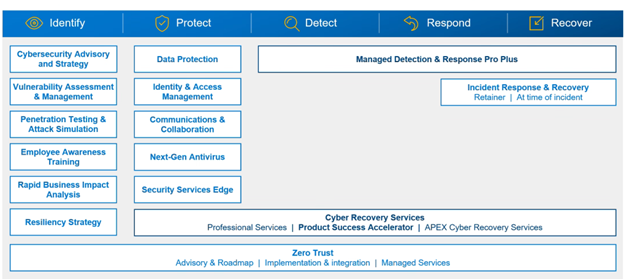
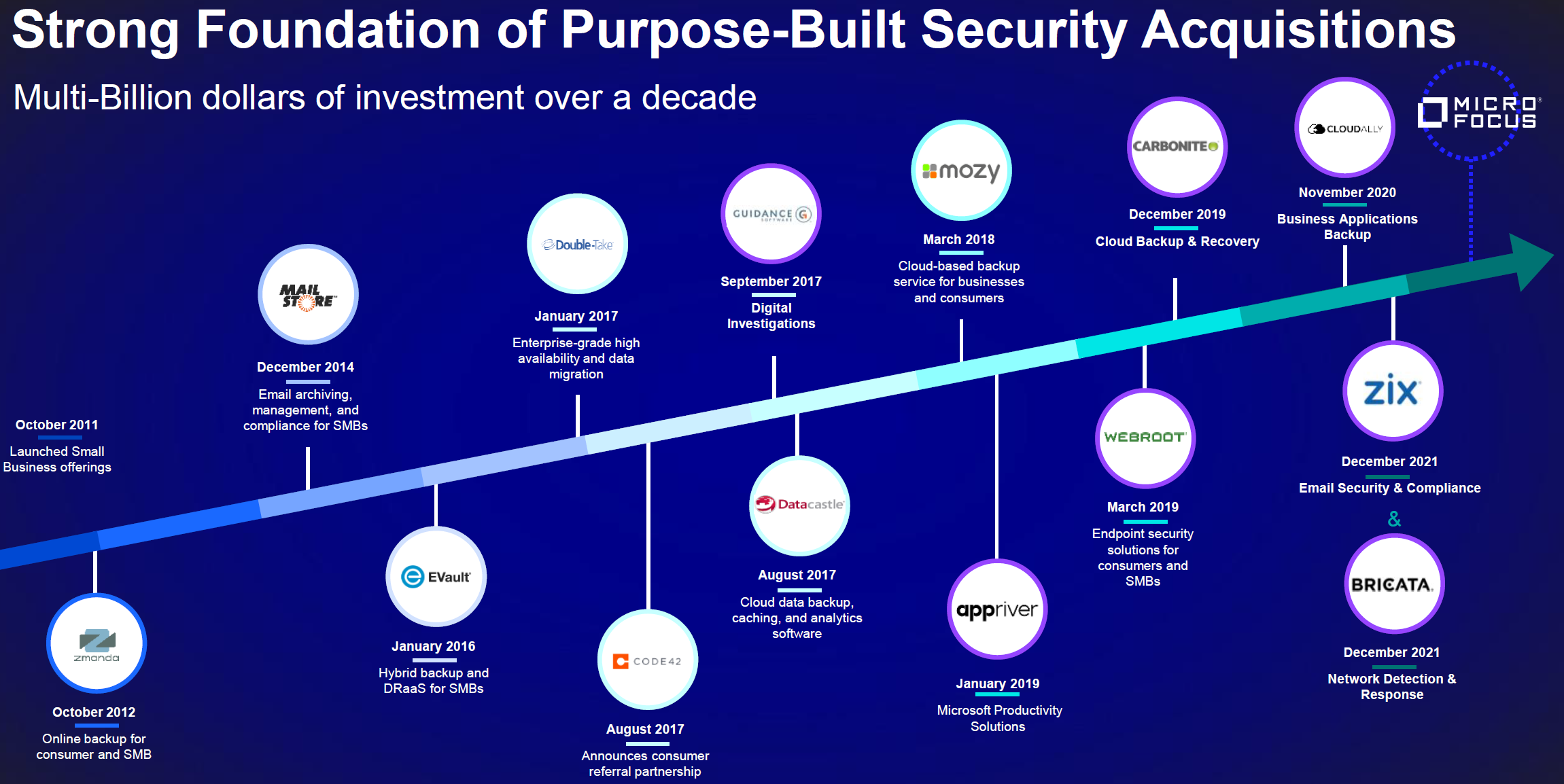
Dell’s recent enhancements to its security portfolio address midmarket companies' specific security concerns and goals. Dell has significantly expanded its security portfolio with in-house capabilities and partnerships to enhance its threat protection, management, and incident response capabilities. The company’s new additions are crucial in addressing mid-market businesses' security challenges. According to Techaisle data, cybersecurity prevention investments are the highest technology priority for core and upper midmarket firms. With an average spending increase of 8.6%, 64% of midmarket firms are boosting their investments in cybersecurity solutions. The main reason for this spending increase is advanced threats and the rise of remote working, as reported by 61% of firms. In today's digital environment, cyberattacks are becoming increasingly prevalent and sophisticated, posing a threat to companies of all sizes. The traditional approach to security revolved around building higher cyber walls, hoping that no one would cross them. However, in the last ten years, attackers have found ways to breach these walls, making it necessary to have preventive strategies in place. Businesses must therefore prepare for the possibility of breaches and their potential impacts. Consequently, they must have a comprehensive security portfolio that offers end-to-end protection – from detecting and preventing threats to minimizing the damage in the event of a breach and helping users recover their data.
Mid-market enterprises are particularly susceptible to cyberattacks due to their limited resources compared to larger organizations. They face the same challenges as their larger counterparts but require more resources to defend themselves. To address these challenges, mid-market businesses need a security portfolio that can protect their operations from cyberattacks and minimize the risk of financial and reputational damage, especially as cyber threats become increasingly sophisticated. This article examines how recent updates to Dell’s security solutions portfolio can help mid-market businesses navigate the evolving threat landscape and enhance their protection capabilities.